On Monday, May 29, 2023, the Chilean Army confirmed to be in active response to a cyber attack detected last Saturday, May 27, which affected different systems within the organization’s internal network. The attack has been attributed to the criminal group Rhysida.
The Chilean Army has confirmed to be under cyber-attack since last Saturday, May 27, 2023, as stated in an official communiqué issued on Monday, May 29, 2023. In the statement, the Directorate of Strategic Communications informs that “the institutional data transmission network was affected by a computer incident”, this attack could be detected thanks to the cybersecurity systems at the disposal of the general secretariat.

As an initial response to the attack, preventive measures were taken, such as not turning on computers, avoiding connection to the VPN network and prohibiting the connection of any type of external storage device. According to the statement, among other measures implemented was the isolation of the network for the start of the corresponding audits. This was carried out by the security agencies to carry out the incident response plan.
The attack carried out against the Chilean army has been a disruptive ransomware attack, this is not only implied in the press release, but also confirmed in parallel by the Government CSIRT. This ransomware attack has been credited to a new group of malicious actors, which has been named Rysida ransomware.
Monitoring by the CronUp team shows that during the weekend of the cyber-attacks, the Army’s websites were intermittently available, which could well be due to the organization’s attempts to isolate and/or protect the corporate network.
RHYSIDA RANSOMWARE
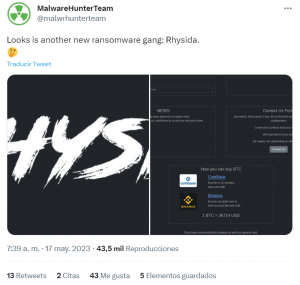
On May 17, 2023, the MalwareHunterTeam announced, through its official Twitter account, a ransomware campaign carried out by a new group of malicious actors calling themselves Rhysida.
The group of threat actors, who see themselves as a “cybersecurity team” attack systems and highlight various potential problems in the victim’s security systems. This “security team” charges a fee for the “service” of finding the various security flaws in the victim’s systems, however, the group also threatens victims with leaking the information collected in an attack through the Dark Web. This is something that has been seen repeatedly in modern ransomware attacks and is referred to as “double extortion or multi extortion”.
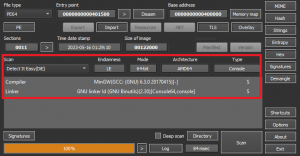
According to a sample analysis conducted by Secplicity. All indications are that the malicious actor group is, in fact, a new emerging group, which is in the early stages of the development cycle. This is based on the functions observed in the sample, such as the lack of many basic functions in the payloads they release, as well as a malfunctioning background image replacement. The sample examined was written in C++ and compiled using MinGW (mingw32). It weighed about 1.2 MB and was not packaged.
It was also observed that the ransomware removes the wallpaper in various ways, however, a “Conttol Panel” type was observed when deleting the wallpaper registry settings via the Control Panel. There is also mention of encryption, as well as a PowerShell invocation with a hidden window.
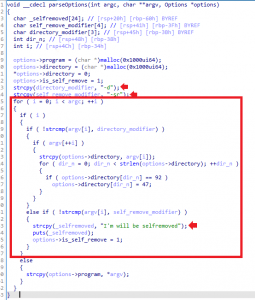
The Rhysida encryptor allows the use of two arguments (-d and -sr), which are defined by the authors as parseOptions. The -d argument selects a directory to encrypt, while the -sr argument, the file deletes itself after execution (I’m will be selfremoved).
After the encryption of the files, victims must contact the malicious actors through the TOR-based portal they offer, making use of Rhysida’s unique identifier, which is provided through the ransom note. When the victim enters their unique identifier in the payment portal, the group will display a form which the victim must fill out with authentication, contact details and other information.
The ransom note is presented as a PDF file with the name “CriticalBreachDetecte.pdf” this ransom note, in a summarized form, mentions that:
- “A security alert has been detected by Rhysida’s cyber security team” states that systems have been compromised and that a significant amount of confidential information has been leaked. They also mention the consequences of this type of leaks, such as the sale or publication of this information.
At the same time, the “team” mentions that there is no need to be alarmed, since it is only necessary to acquire the unique key that they have developed, so that all the information can be recovered. This key is sent through their TOR portal. At the same time, the team warns that any attempt to decrypt the encrypted information may result in the total loss of the information.

However, the Rhysida leak site, hosted on the Dark Web, has yet to feature any of the group’s victims. It is known that the group is actively carrying out attacks and is in constant development.
Indicator of Compromise
| Indicator | description |
| MD5 | 0c8e88877383ccd23a755f429006b437 |
| SHA1 | 69b3d913a3967153d1e91ba1a31ebed839b297ed |
| SHA256 | a864282fea5a536510ae86c77ce46f7827687783628e4f2ceb5bf2c41b8cd3c6 |
| Original file name | fury_ctm1042.bin |
It is worth mentioning that the aforementioned indicators of commitment are NOT those that were observed in the attack against the Chilean Army, as the relevant investigations on this attack are still ongoing.



