A new exploit targeting the VMware ESXi Shell service is circulating on several hacking forums, posing a significant risk to organizations that use VMware for their virtual environments. This exploit, known as #ESXiVortex, can allow unauthorized access and control over virtual machines, with potentially disastrous consequences for businesses. Here we analyze the exploit and provide steps to protect your systems.
EXPLOIT DETAILS
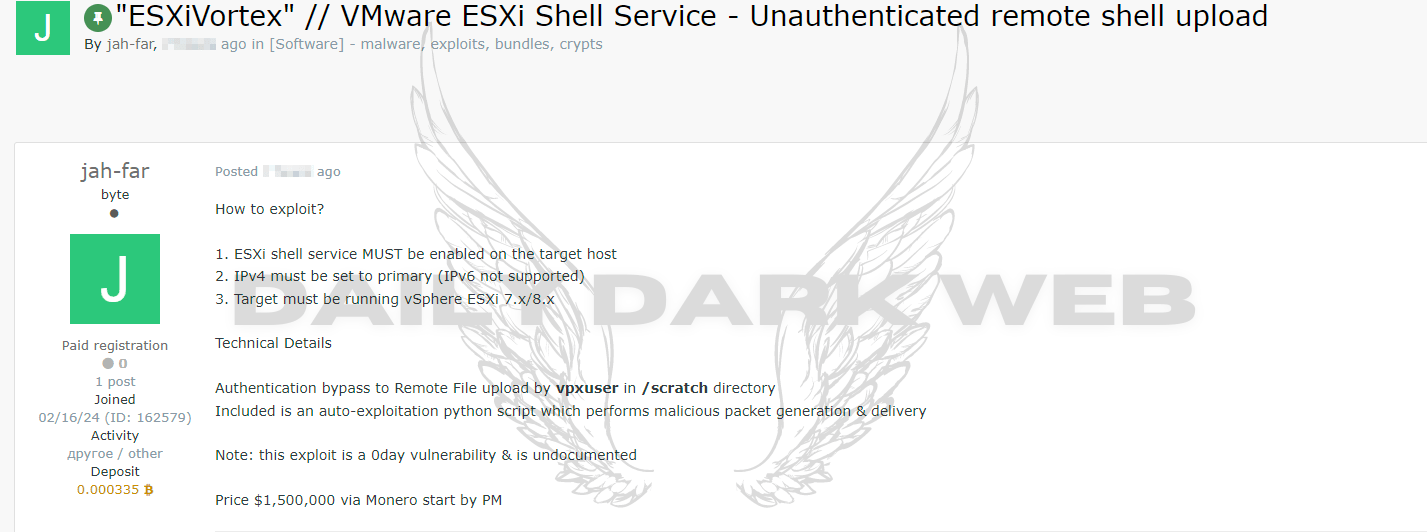
The exploit specifically targets the VMware ESXi Shell service in versions 7.x and 8.x. This service provides a command line interface for direct interaction with the host, so a vulnerability in this area can be extremely dangerous. The exploit was made public in February 2024 and is sold for a price of $1,500,000 through Monero. To execute the exploit, the ESXi shell service must be enabled on the target host, IPv4 must be the primary network protocol, and the target system must be running vSphere ESXi 7.x/8.x.
POTENTIAL CONSEQUENCES
The Zero-Day exploit allows you to bypass authentication and upload files remotely to the /scratch directory, using the vpxuser user. If the exploit is successfully executed, attackers could gain control over all virtual machines hosted on the server, leading to a massive breach of internal and customer data. Additionally, the outage could impact critical operating systems, resulting in significant downtime and financial losses for the company.
MEASURES TO PROTECT YOUR SYSTEMS
Check System Version: The first step for administrators is to check the current version of their VMware ESXi installations. If you are running versions 7.x or 8.x, you should consider taking steps to protect against this vulnerability.
Apply Patches Immediately: If systems are found to be vulnerable, it is critical to apply patches provided by VMware immediately. These updates are designed to close the security loophole and prevent potential vulnerabilities.
Monitor Network Activity: Continuous monitoring of network activity can help detect unusual behavior. This is essential to detect and mitigate any exploitation attempts early.
Periodic Security Audits: Regularly scheduled security audits and compliance checks can help ensure that no vulnerabilities are left unaddressed. This helps keep systems secure over time.
CONCLUSION
Organizations using VMware ESXi should take immediate steps to patch their systems to protect against this serious security threat. The #ESXiVortex exploit poses significant risks to information security and business continuity, so vigilance and quick action are essential to mitigate its impact.



