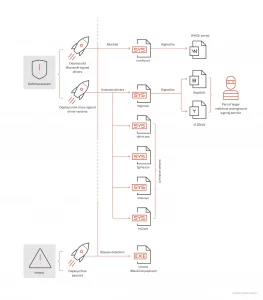
The ransomware group called ALPHV, also known as BlackCat, has been seen making use of malicious Windows kernel drivers to evade detection by security software during an attack.
It is not uncommon to see malicious actors making use of different approaches to sign their malicious kernel drivers, usually by abusing Microsoft signature portals, making use of leaked or stolen certificates, or through underground services.
In a February 2023 ransomware incident, we observed evidence of ransomware operators and affiliates who have a strong interest in gaining privileged-level access to the ransomware payloads they use in their attacks. Typically, these groups make use of ransomware bypasses with low-level components to evade detection. After a kernel-level approach to these attacks, it was noted that most payloads are found during the defense evasion phase.
Some ransomware attacks attempt to meet code-signing requirements by Microsoft, which allows the attacker to compile kernel modules designed for very specific tasks before releasing the actual payload. Ransomware operators can adopt one of the following approaches:
- Using a code signing certificate that has been leaked, stolen from a compromised environment, or obtained from an underground market.
- Obtain a new certificate by impersonating a legitimate entity and following Microsoft processes to obtain the cross-signed certificate. Abuse the Microsoft portal to issue signed kernel modules and request valid code signing certificates.
BlackCat in February, appear to be an improved version of the previously seen malware called POORTRY. POORTRY was used by UNC3944, a group of hackers, also known as “Oktapus” and “Scattered Spider”. The main function of this malware was to terminate all security software running on a Windows device to evade detection.
In comparison, the new driver used by the BlackCat operation allows elevation of privileges on compromised machines, and subsequently terminates all processes related to security agents.
DRIVER SIGNATURE
The driver signature seen in the attack by BlackCat in February 2023 is “ktgn.sys”. However, there are a wide variety of driver signatures being used by BlackCat affiliates in the detection evasion phase, as shown below.
The user agent tjr.exe, which is protected by a virtual machine, drops the kernel driver into the temporary user directory C:\%User%\AppData\LocalTempKtgn.sys. It then installs the driver with the name ktgn and the initial value = System (this way it will start when the system reboots).
The malicious kernel driver exposes an IOCTL (input/output control) interface, which allows the user-mode client, tjr.exe, to perform commands, which will be executed by the driver with Windows kernel privileges. This client supports ten different commands, each with a specific function, which are executed from the kernel driver, through the appropriate IOCTL interface. The commands that the driver can perform are:
- Activate driver
- Deactivate driver after the client in user mode concludes its operation.
- Kill process
- Delete files
- Force file deletion
- Copy file
- Force file copy
- Log process/thread notification
- Unregister process/thread notification
- Restart system
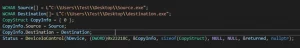
In reference to the registration and de-registration of process/thread notification, it is indicated that both ways are inaccessible, which would indicate that they are still in the development or testing phase.
The use of rootkits by malicious actors to hide malicious code from security tools is a trend that seems likely to continue to increase as attacks become more sophisticated, especially by groups with the necessary skills to implement them.
So, the main danger lies in the ability of this type of rootkit to hide complex, targeted attacks that are used in the early stages of a Kill chain, giving the attacker the opportunity to disarm all the defenses of a system and then launch the actual payloads.
IOCs
| File name | Hash | detection name |
| Yixowv.exe | 17bd8fda268cbb009508c014b7c0ff9d8284f850 | Ransom.Win32.BLACKCAT.SMYPCC5 |
| Cor.exe | 78cd4dfb251b21b53592322570cc32c6678aa468 | Ransom.Win32.BLACKCAT |
| Trj.exe | c2387833f4d2fbb1b54c8f8ec8b5b34f1e8e2d91 | Trojan.Win64.STONESTOP.A |
| Dkrtk.sys | 91568d7a82cc7677f6b13f11bea5c40cf12d281b | Trojan.Win64.VMPROTECT.R002C0RA |
| Fgme.sys | 0bec69c1b22603e9a385495fbe94700ac36b28e5 | Troj.Win32.TRX.XXPE50F13019 |
| Ktes.sys | 5ed22c0033aed380aa154e672e8db3a2d4c195c4 | Troj.Win32.TRX.XXPE50F13019 |
| Kt2.sys | cb25a5125fb353496b59b910263209f273f3552d | Troj.Win32.TRX.XXPE50F13019 |
| Ktgn.sys | 994e3f5dd082f5d82f9cc84108a60d359910ba79 | Rootkit.Win64.POORTRY.A |



